8.3 Social issues
|
Previous
Chapter 7: Computer management
|
Next
Chapter 9: Internet services
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
 Learning outcomes
Learning outcomes
At the end of this chapter you should be able to:
- describe and give an overview of the internet
- explain what is needed to connect to the internet
- describe and give an overview of the World Wide Web
- describe and explain social issues with the internet
- understand the functions of browsing and searching.
INTRODUCTION
In the previous chapters you have learnt a lot about the internet and the different types of networks, the networking equipment and some of the electronic communications that uses the internet.
UNIT
8.1 The internet and world-wide web
The internet is the world’s largest WAN and is made up of various nodes that connects via communication media all over the world. This allows all nodes to connect and communicate with one another. It also allows for various services, such as the world wide web and email to be hosted over or work on the internet.
INTERNET ADDRESSES
Each day there are over a billion emails and search requests sent over the internet. But how does the data know where to go? How do we make sure that the data goes to the intended receiver and the correct destination?
Every computing device that is connected to the internet receives a unique address, much like your street address. This address is called, an internet protocol address or IP? address. Whenever a message is sent over the network, it is sent to a device’s IP address. The most common type of IP address is known as an IPv4 (internet Protocol Version 4) in which each number can range between 0 and 255, and is be represented by 1 byte (or 8 bits) of information. The IP address is made up of four sets of these numbers, separated by dots. This is shown in Figure 8.1 alongside:
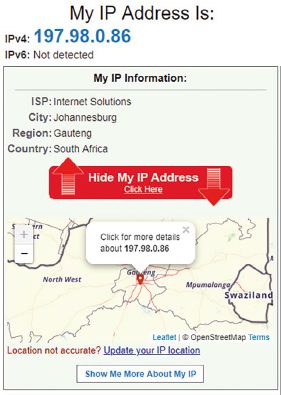
IP addresses are difficult to remember. For example, an IP address for Facebook could be 185.60.219.35, while an IP address for Google could be 216.58.223.3. To make it easier to find a specific website or, websites make use of domains.
A domain is a unique name that may be linked to an IP address. A domain name is the part of a network that identifies itself as belonging to a particular person or company, for example, the SABC, SARS, and so on.

IP ADDRESSES EXPLAINED
INTERNET CONNECTION
In order to connect to the internet, you need to have an internet service provider (ISP). The ISP will charge you a fee and in return, permit your device to use their network to connect to the internet. Most ISPs may also offer to help clients setup internet services connections as part of their service offering.
INTERNET SERVICE PROVIDERS (ISPS): WIRED AND WIRELESS CONNECTIONS
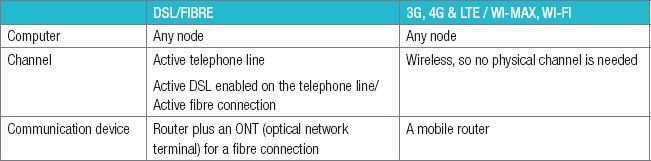
ISPs can provide you with either a wired or a wireless connection to the internet. In most cases, your ISP will provide you with the hardware you need to connect to the internet. However, if this is not part of their service offering, you will need to ensure you have the following hardware equipment:
- a computing device
- the internet connection channel
- an internet communication device.
The table below summarises the hardware needed for the different types of internet.
Table 8.1: Equipment needed for the different types of internet
THE WORLD WIDE WEB
The world wide web (WWW) is a collection of websites that you can browse or access through the internet using a web browser. If you think about the IP address as a company’s physical address, a website on the WWW will be that part of the company that customers can see.
WEB ADDRESSES AND THE ADDRESS BAR
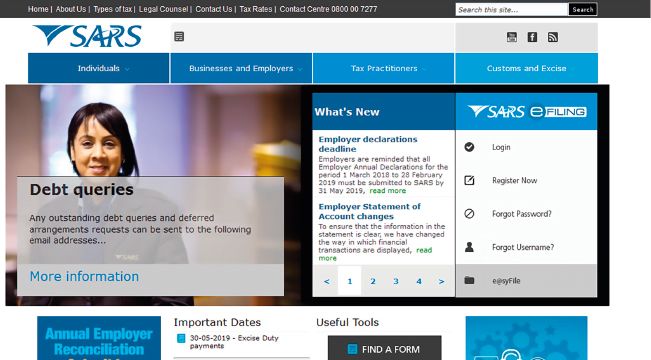
Each webpage on the internet has its very own address called a uniform resource locator (URL), which indicates to the internet exactly what page you want to see on a website. When you type a URL in the address bar of the web browser and press ENTER, the browser will take you to that specific page. For example, in the figure below, we typed www.sars.gov.za in the address bar, which then loaded the South African Revenue Services (SARS) webpage.
In the following example, you will learn more about URLs.
Example 8.1
Each segment in an URL is a part that makes up the web address.
The domain name is the most important part of an internet address. This could be a word or a phrase that an internet site has identified as the name of the website. People use it to find information on the internet, for example businesses use it to get people to visit their websites.
http://www.sars.gov.za/ClientSegments/Individuals/How-Send-Return/

A webpage is a single page of a website. Hypertext mark-up language (HTML) is a type of coding language used on a webpage that enables the display of text, multi-media and other interactive content. The web browser is a piece of software that can interpret the HTML code and display the content as we see it on a webpage. A website consists of a collection of many of these HTML-coded webpages that are connected together. When you have accessed a secure website you will see that the http prefix has changed to https. You should check for this before making any electronic payments online.
 Activity 8.1
Activity 8.1
8.1.1In your own words, define the internet.
8.1.2What have you personally used the internet for?
8.1.3What is an IP address?
8.1.4Is the IP address the same on all devices? Give a reason for your answer.
8.1.5Why do computers have IP addresses?
8.1.6Explain the use of a domain name.
8.1.7Tabulate and compare the equipment you need to access the internet for fibre and 3G.
8.1.8The URL for New York Public Library is: https://www.nypl.org/events/programs/2019/08/03/create-website-html-and-css
a.Identify the three key elements of a URL.
b.Using the information in the URL, explain what information could be displayed on the webpage.
c.Is this a secure site? Explain.
8.1.9What does the following URL tell you? http://publicdomaintorrents.info/nshowcat.html?category=animation
UNIT
8.2 Browsing and searching
In this unit, you will learn about browsing and searching the internet.
A browser is an application designed specifically to access and display webpages, including the webpage's content such as text, images and videos.
EXAMPLES OF WEB BROWSERS
The five most popular web browsers are:
- Google Chrome
- Mozilla Firefox
- Microsoft internet Explorer
- Microsoft Edge
- Apple Safari.
ACCESSING A WEB BROWSER
In order to open your web browser, select your web browser icon (Any of the listed browsers). Once your browser is open, you need to decide which website you would like to visit. This is done by either:
- browsing to the correct website
- searching for the correct website.
The next section will show how the different methods of browsing can achieve the same results – they may just be easier or more difficult to use.
BROWSING
When you browse a website, you need to know its unique web address (such as https://en.wikipedia.org for the Wikipedia website). Once you know the address, you can visit the website as follows:
Step 1: Open your web browser.
Step 2: Enter the website’s address or URL in the address bar at the top of your browser.

HOW DO WEB BROWSERS WORK?
Step 3: As soon as you press Enter, the webpage should begin to load.
Step 4: Once loaded, you can browse the website by clicking on buttons, links or following the instructions on the page.

Did you know
Anything on a website can be a link. Whenever your cursor moves over a link, the cursor will change from an arrow to a small hand.

THE INTERNET: HOW SEARCH WORKS
SEARCH ENGINES
Searching: you may want to search the internet for specific answers or try to find new, interesting websites to explore. To do this, you can use a search engine to find the information you are looking for.
Two popular search engines are:
- Google (www.google.com)
- Microsoft Bing (www.bing.com)
Google is the most popular, powerful and easy-to-use search engine of the two. In fact, Google’s search engine has become so well known that ‘to Google something’ has become a verb that means to search for something. In future, if someone asks you a question that you do not know the answer to, you can tell them to just ‘Google it’.
Microsoft’s Bing search engine is also a very popular English search engine and this is all thanks to its integration with Microsoft Windows.
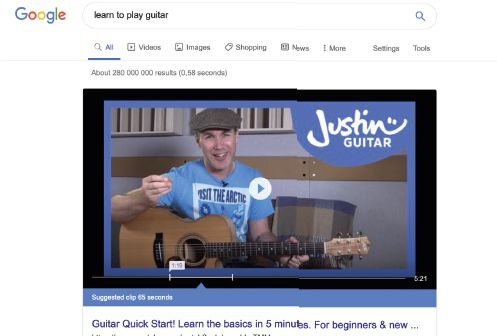
In order to search for information on the internet, enter the search engine’s address in your address bar. Once the search engine loads, there will be a space on the page for you to enter your search criteria. For example, if you want to find a website to teach you how to play the guitar, you may search for the phrase ‘learn to play guitar’ and press Enter.

Did you know
Your web browser will search for any information you enter the address bar that is not a web address. For example, if you type ‘Learn to play guitar’ into the Google Chrome or Bing address bar, the search-engine will search for websites that teach you how to play guitar. These pages will be ranked with ‘most popular’ first.
As the figure above shows, the search engine found 280 000 000 webpages that can teach you how to play the guitar! By clicking on one of these links, the search engine will take you to the specific website you selected. The search results displayed to you will include images, videos, maps, shopping, books, music and so forth. The results all depends on the type of information and format that is available on the search engine.

Did you know
While the first result is usually the best result, companies can pay search engines to have their website advertised above the first search result. While these advertisements can look like a normal search result, they will always be marked as an advertisement or promoted search result.
SEARCH TECHNIQUES
Search engines search through billions of webpages stored on hundreds of millions of websites to ñd information matching your search. Most search engines try to place the best options near the top of the search results, with the results becoming worse as you move to the second and third pages.
Since the first search results are usually the best, if you do not find what you are looking for on the first page or two of the results, you should try a different search phrase or try to use an advanced search technique.
The table below highlights a few of the most useful search techniques.
Table 8.2: Search techniques
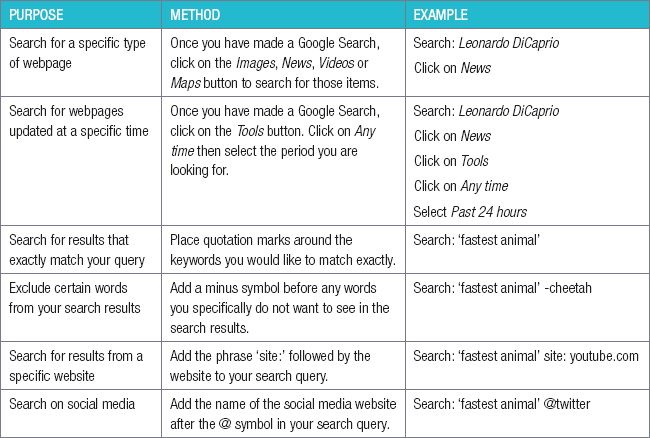
These techniques can be very useful. However, thanks to improvements in search engines, you should generally find the information you are looking for without requiring any additional techniques. When you find a website that you would like to use again in the future, you can bookmark the URL. This will place it on a favourites list in the web browser for easy access in the future. In Google Chrome and Edge you simply click on the star shape to the right of the URL in the address bar to create a bookmark.
THE WORLD WIDE WEB CONSORTIUM
The World Wide Web Consortium (shortened to W3C) is the organisation that is responsible for setting standards for the world wide web. By following the W3C standards, web designers can ensure that their webpages display correctly on any browser. This also helps computers to do more useful work over the world wide web.
 Activity 8.2
Activity 8.2
8.2.1Which of the following is an example of a web browser?
a.Mozilla Firefox
b.Google
c.Linux
d.Microsoft Outlook
8.2.2When you are looking for interesting websites to explore, you use a _____ to find the answer.
a.browser
b.bookmark
c.search engine
8.2.3Which of the following is NOT an example of a search engine?
a.Google
b.Google Chrome
c.Microsoft Bing
8.2.4The first result found is always the best result.
a.True
b.False
8.2.5What is a web browser?
8.2.6If you are looking for something specific on the WWW, how do you decide which website you would like to visit?
8.2.7How do you know that something on the webpage is a link to another website/page?
8.2.8What do you do if you want to search for webpages that were updated within a certain time?
8.2.9What do you do if you want to search for results that exactly match your query? Give an example.
8.2.10What do you do if you want to search on social media?
8.2.11For this activity, you will need a computer with access to the internet.
a.Use the following URLs to browse the internet. Give at least two examples of what you found on each website.
i.https://www.conservationinstitute.org/10-fastest-animals-on-earth/
ii.https://www.pcgamer.com/new-games-2019/
iii.https://www.livescience.com/33316-top-10-deadliest-natural-disasters.html
b.Using any search engine, find at least two websites per topic and write down their URLs:
i.the biggest spider
ii.the best rapper in South Africa
iii.artificial intelligence.
8.2.12For this activity, you will need a computer with access to the internet. Using web searches, find answers to the following questions:
a.What is the second fastest mammal in the world?
b.On what day was the first telephone call made?
c.Who is the richest person in the world and what is his or her job?
d.Which film made the most money of all time?
e.How old would Nelson Mandela have been today (in years)?
f.Which YouTube channel has the most subscribers?
g.Which YouTube video has the most views?
h.How tall is Mount Fuji?
i.How many people live in South Africa’s largest city?
j.Which artist has sold the most albums?
Once you have found the answers, your teacher will share the correct answers with the class. Did you get them all right?
8.2.13Based on the previous activity, discuss the following topics:
a.Why did different people get different answers?
b.Were the websites with inaccurate answers incorrect, outdated, or did they answer a different question?
c.Were any of the teacher’s answers incorrect or outdated?
d.How do you think people kept up to date with information before the internet?
UNIT
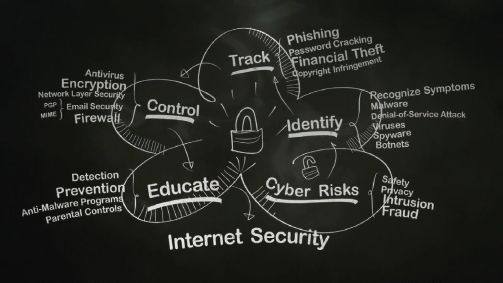
8.3 Social issues
In this unit you will learn a bit more about the different types of security threats. You will also learn how you can protect yourself from these threats when browsing the internet and opening emails.
We use computers and smartphones to do just about anything. This ranges from transferring money through online banking to getting ID documents and passports. As a result, if someone can gain access to a person’s computer and password, they can gain access to their bank account, identity and their photos. They can also use their computer to send spam emails and add unwanted advertisements. Because of this, computer users need to understand the basics of computer malware (malicious software) and know how to use computers and the internet safely.

FAKE NEWS
Never react to any news until you have checked it against at least one other reputable news site, and remember to never share fake news, not even as a joke! False news stories, which are often of a sensational nature, are created to be widely shared online for the purpose of generating ad revenue via web traffic or discrediting a public figure, a political movement, a company, a fringe organisation and so forth. In order to spot fake news, you need to understand what real news looks and sounds like. Getting into the habit of visiting trustworthy news sites is one way to become familiar with real news.
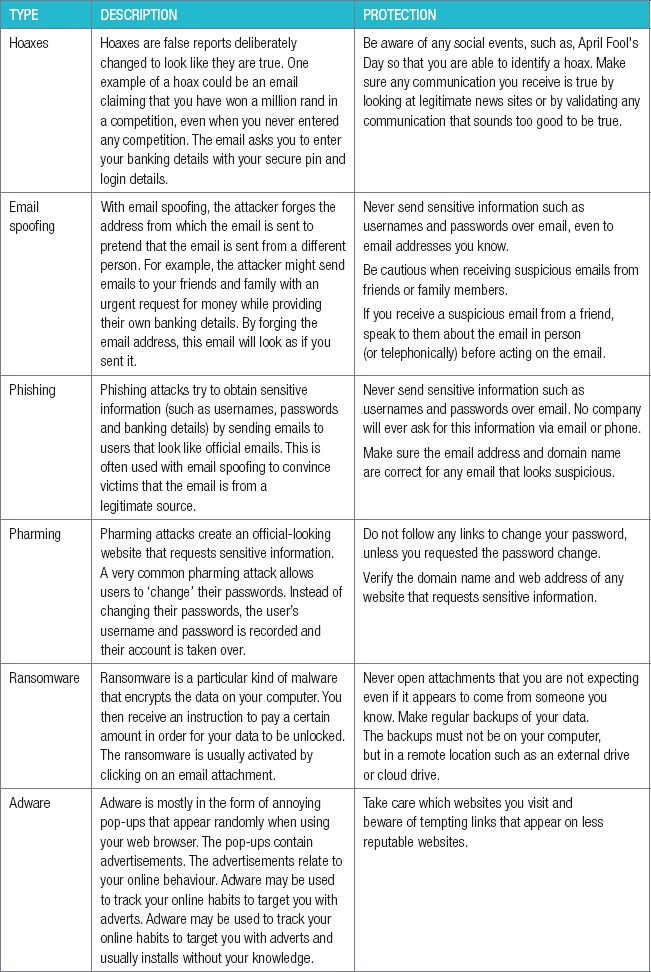
TYPES OF THREATS
Not all types of computer threats work in the same way or have the same goals. The table below lists some of the most common threats in the world today, as well as the best way to avoid them.
Table 8.1: The most common threats

SAFE EMAIL AND INTERNET USE
In order to avoid threats, computer experts suggest following these guidelines:
- use a secure password
- pay careful attention to the websites and links you open
- do not share your sensitive information unnecessarily
- do not open suspicious emails.

10 TIPS TO PROTECT YOURSELF ON THE INTERNET

EMAIL ETIQUETTE
ETIQUETTE FOR E-MAILS
Netiquette is short for network and e-mail etiquette. Netiquette refers to the use of good manners when communicating electronically or when using the internet, whether it is in the workplace or on a personal level. This includes respecting other people’s privacy.
Look at the following guidelines to practice good netiquette:
- Messages: Do not spam people at work, your friends or family with unwanted e-mail messages or chain e-mails. Spam is unwanted or irrelevant messages that are sent over the internet or through e-mails.
- Concise: Make sure that when writing e-mails, it is clear and to the point. Also make sure that it does not contain spelling and grammatical errors.
- Subject line: Make sure the subject line is clear so that the recipient knows what the e-mail is about.
- Identify yourself: Always say who and what you are at the beginning of the e-mail and add your signature at the end of the mail.
- Action required: Let the recipient know right away if any action is required from their side. You can do that by marking e-mails that do not require any action with FYI in the subject line.
- Capital letters: Do not type e-mails in capital letters as it gives the recipient the idea that you are shouting.
- Exclamation marks: Avoid using exclamation marks or use them sparingly. The use of exclamation marks sends a message to the recipient that you are demanding.
- Large attachments: Compress large files before sending them. This helps the recipient to save time instead of waiting for a long time to download files. You can always ZIP or compress files (as learnt in Chapter 5) to make it easier to send.
- Gossip, inflammatory remarks and criticism: Avoid gossiping about others through e-mail, especially at the workplace. Also, do not send insulting, abusive or threatening e-mails. You cannot withdraw such an e-mail and it can easily be forwarded to unintended recipients. This could lead to unnecessary disputes and grudges in the workplace and in your personal environment.
- Focus on what is in the e-mail: Make sure that you read the e-mail properly and address the sender’s questions.
- Proofread the text: Before sending the e-mail, read through it again to make sure that it is saying what you want it to say and that there are no spelling and grammar mistakes.
 Activity 8.3
Activity 8.3
8.3.1Indicate whether the following statements are TRUE or FALSE. Write ‘true’ or ‘false’ next to the question number. Correct the statement if it is FALSE. Change the word(s) in bold text to make the statement TRUE. You may not simply use the word ‘NOT’ to change the statement. NO mark will be awarded if only FALSE is written down.
a.A virus is any program that infects a user’s computer and acts in a way that will harm the user without the user’s knowledge.
b.Phishing attacks create an official-looking website that requests sensitive information.
c.With adware, the attacker forges the address from which the email is sent to pretend that the email is sent from a different person.
d.Ransomware is a particularly malicious virus that locks all a user’s files and encrypts data on the computer.
e.Freeware is a type of virus that creates unwanted advertisements all over a user’s computer.
f.Email spoofing refers to irrelevant, unsolicited emails sent over the internet, typically to many users.
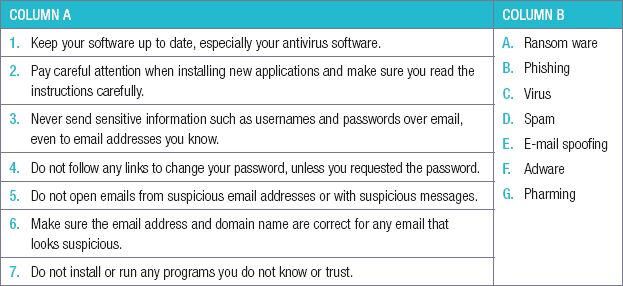
8.3.2Choose a term/concept from COLUMN B that matches a description in COLUMN A. Write only the letter next to the question number (e.g. 1.1– A). there can be more than one answer to a question. To prevent threats, you must do the following:
8.3.8List the steps you can take to keep your internet usage safe in order of importance, according to your opinion. Support your answer.
8.3.9In 2014, photos were obtained by a hacker who created an email account called ‘Apple Privacy Security’ and sent emails to hundreds of celebrities asking to verify their security information. While many celebrities did not respond, those who did provided sensitive security information that could then be used to crack their passwords or change their passwords. Once the hacker had access to the celebrities’ Apple accounts, he looked through their personal photos and shared them on the internet.
Based on this case study, answer the following questions.
a.List and describe the two hacking techniques the hacker used to gain access to the celebrities’ photos.
b.How could the celebrities have prevented these attacks?
c.The accounts of celebrities who did not provide any sensitive information were still hacked after the hacker successfully guessed the correct password.
i.How could these celebrities have created a better password?
ii.Give an example of a more secure password. Note: Do not give your own password!
iii.How likely do you think a hacker, who knows everything about you, would be to guess this password?
d.How would two-factor authentication have prevented this hack?
CONSOLIDATION ACTIVITY Chapter 8: The internet and world-wide web
Choose the correct answer.
1.What is the internet
a.The world’s largest wide area network.
b.The same as the World Wide Web.
c.Both A and B
2.What is the URL?
a.It is a domain name.
b.It is the unique web address of a webpage.
c.It is an internet protocol.
3.What is an ISP?
a.An ISP is used to identify the webpage that you would like to connect to when browsing the internet
b.An ISP primarily provides a connection to the internet as its main service.
c.An ISP is used to allow devices to connect to the internet without using an IP address
4.You will need the following equipment to connect via a fibre line to the internet.
a.A computer, router, USB dongle, ONT device
b.A computer connected to a router, active telephone line, ONT device
c.A computer, an active fibre connection and an ONT device and a router
5.Which are the five most popular web browsers.
a.Apple Safari, Google Chrome, Microsoft Edge, Microsoft internet Explorer, Mozilla Firefox
b.Mozilla Firefox, Google Chrome, Google, Microsoft Edge, Microsoft internet Explorer
c.Microsoft Edge, Microsoft internet Explorer, Microsoft Bing, Google Chrome, Google
6.When you place quotation marks around the keywords you would like to match exactly, you are _____ ?
a.Searching on social media.
b.Searching for results from a specific website.
c.Searching for results that exactly match your query.
7.The attacker sends emails using your email address to your friends and family with an urgent request for money while providing their own banking details. This is called _____?
a.Phishing
b.Email spoofing
c.Spam
8.What must you do to avoid safety and security threats.
a.Use a password that is easy to remember but difficult to hack.
b.Use two-factor authentication whenever possible.
c.Do not download an attachment if you do not know who the sender of the email is.
d.All three of the above
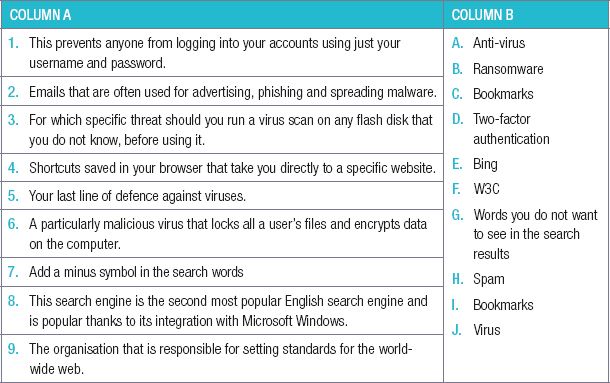
9.Choose a term/concept from COLUMN B that matches a description in COLUMN A.
Write only the letter next to the question number (e.g. 1– A). There can be more than one answer to a question.
11.Using your understanding of URLs, see if you can figure out which webpages the following URLs are accessing:
iii.https://www.google.com/mail
iv.https://www.facebook.com/messages/
v.https://www.google.co.za/search?q=computers
12.List and describe two search techniques.
13.What are bookmarks?
14.According to the World Wide Web Consortium (W3C), websites should be evaluated according to four criteria.
a.W ho is the W3C and what is their purpose?
b.Today, most restaurants understand the importance of having a business website that provides users with information on the restaurant, its menu, its specials and any opening or closing times. For example, the website of the popular South African restaurant, Mugg & Bean, can be found at https://themugg.com/. Based on this information, answer the following questions.
c.A website’s address is made up of three key elements. What are they?
d.Mugg & Bean’s website uses the HTTPS protocol. What is the difference between HTTP and HTTPS?
e.Online shops mostly use the HTTPS protocol. Why do you think this is?
f.Hackers often try to hack into online shopping accounts.
i.Which hacking techniques can they use to hack your account? List and describe how each technique can be used.
ii.How can you create a password that is not easily cracked?
iii.Can Adware be used to hack into your online shopping account? Give reasons for your answer.
15.Thanks to a new infrastructure in your area, your parents can upgrade your internet from 4Mb DSL to a 100Mb fibre line. However, before they can do that you need to give them some advice first. To do this, answer the following questions:
a.Will your parents need to find a new ISP for their fibre internet? Give a reason for your answer.
b.What additional hardware will your parents need for the fibre?
c.What hardware or connections will your parents no longer need for DSL?
d.How will the new fibre internet be connected?
16.After Tsekiso has struggled with a slow mobile internet for a few months, he decides to change his mobile internet service provider. Answer the following questions on internet service providers.
a.What is the purpose of an ISP?
b.How can an ISP help you to set up an internet connection?
17.Enrichment activity – this activity is optional.
Working together with at least one but preferably two classmates, you need to do research on internet options available to you, before presenting your findings to the class. To do this, decide what speed internet and how much data you would need if you shared the internet with each other.
a.Do research on different internet packages that can satisfy your requirements. Each group member should analyse at least one internet package.
b.For each package, you should answer the following questions:
i.What is the internet speed?
ii.What is the data cap?
iii.Are there any terms and conditions you should be aware of?
iv.Is the required hardware included in the package?
v.Is the package a long-term contract or a month-to-month deal?
vi.What is the cost of the package?
vii.Are there any additional costs you will also need to pay (such as a telephone line rental)?
c.Once you have two to three viable options, decide what the best internet package will be.
d.Present the packages you investigated, your selected package and the reasons for your choice to the rest of the class.
|
Previous
Chapter 7: Computer management
|
Table of Contents |
Next
Chapter 9: Internet services
|






