10.4 E-commerce and e-banking
|
Previous
Chapter 9: Errors and bugs
|
Next
Chapter 11: Internet and the World Wide Web
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 10.1 | Social-engineering tricks |
| Unit 10.2 | Data protection |
| Unit 10.3 | Protecting yourself online |
| Unit 10.4 | E-commerce and e-banking |
| Unit 10.5 | How antivirus programs work |
 By the end of this chapter, you will be able to:
By the end of this chapter, you will be able to:
- Identify different social-engineering tricks
- Describe why data backup is important
- Back up data correctly
- Discuss how to avoid online harassment and what to do if you become a target of online harassment
- Describe what malware is and how to avoid it
- Explain multi-step verification
- Describe how antivirus and antimalware programs work
INTRODUCTION
The internet is one of the most amazing inventions of our modern age. At the click of a button, you have access to millions of people across the world. Using a simple search, you can access information. You can learn almost anything on the internet and can teach yourself everything from simple activities such as cooking to more complex things such as making your own furniture.
But there is also a dark side to the internet. Digital crimes are carried out by criminals like hackers who want to steal your information and data, and cyberbullies and stalkers who harass people online. Knowing how to protect yourself from these criminals and crimes is an important part of your online life.
In this chapter, you are going to look at what social engineering is and learn about social-engineering tricks. You will learn about online harassment and how to avoid cyberbullying and cyberstalking. There is also advice on how to shop and bank online safely.
There is a section that discusses what antivirus software is and how it works, and you will also learn how to back up your data for your safety.
UNIT
10.1 Social-engineering tricks
Social engineering is a technique used to gain access to a facility’s systems, data and anything else by exploiting basic human psychology.

HOW HACKING WORKS
This is how a hacker hacks you using simple social engineering:

Some of these tricks include:
- Phishing is usually done via email where an attacker tricks people into giving out personal information or handing over money. Phishing is used with email spoofing and website spoofing. The most common phishing scam is an email from your bank to say your account has been suspended and that you need to reset the password by clicking on a link that takes you to a website that looks like your bank’s website. When you enter your account details, the attacker will have your information.
- Phishing and email spoofing: Phishing and email spoofing attacks try to obtain sensitive information (such as usernames, passwords and banking details) by sending emails to users that look like official emails. These emails will either directly request the sensitive information, or redirect users to an official-looking website from where their information will be stolen.
- Pharming: Much like phishing, pharming attacks create an official-looking website that requests sensitive information. A very common pharming attack allows users to “change” their passwords. Instead of changing their passwords, the user’s username and password are recorded and their account is taken over.
According to security studies, social engineering is the single most effective way to gain illegal access to a desired computer.

SMS PHISHING SCAMS
WHAT TO DO WHEN YOU SUSPECT YOU ARE A VICTIM?
If you think you accidentally revealed any financial information, immediately contact your bank and have them put a hold on any accounts that may be compromised.
Immediately change your password if you think you might have revealed it.
 Activity 10.1
Activity 10.1
Do the following activity on your own.
1.Read through the following case study:
Kevin Mitnick is known as the world’s most famous hacker. He was one of the first computer hackers to be prosecuted and labelled as a computer terrorist, after leading the FBI on a three-year manhunt for breaking into computer networks and stealing software from Sun, Novell and Motorola.
Mitnick started hacking when he was only 16 or 17 years old and later became known more for his use of social engineering to get access into networks than actually hacking them. For example, he called an employee of Motorola and convinced her to send him the code for one of the Motorola cell phones. With this, he was able to use an elaborate social-engineering scheme by manipulating the telephone network and setting up call-back numbers within Motorola’s campus. He even convinced a manager in operations to tell one of the employees to read off his SecurID code any time he needed it, so that he could access the network remotely.
He also managed to hack into their development servers for cell phones and find the source code to all the different cell phones.
When Mitnick was eventually arrested in 1995, he was held for four-and-a-half years without a trial. In the end, he signed a deal and admitted to causing between $5 million and $10 million in losses to Motorola and other companies, although he kept saying that the purpose of his hacking was never for personal gain – he did it for the fun of being able to do it.
After he was released in 2002, he became a security consultant who is now doing exactly what he did as a hacker, i.e. breaking into computer and network systems, but with the company’s knowledge and authorisation.
2.Scan the QR code on the left to watch an interview with Kevin Mitnick.
3.Discuss the following questions in groups:
a.What is social engineering?
b.Discuss four of the types of social-engineering techniques.
i.What is it?
ii.How is it used?
iii.Have you or anyone you know been targeted by social-engineering tricks? What happened?
iv.What can you do to prevent yourself from becoming a victim?

MITNICK INTERVIEW
UNIT
10.2 Data protection
It is important to back up your data regularly, since hardware can fail or accounts can be compromised. Backing up data lets you protect and store information.
CREATING A BACKUP
Because a back up is simply a copy of your computer’s data, it can be created using the Copy and Paste functions.
 Guided Activity 10.1
Guided Activity 10.1
To do this, you should:
1.Start by setting up a backup schedule to work out how often you will create a backup.
2.Buy an external hard drive to use for the backup.
3.On the scheduled backup day, connect the external hard drive to your computer.
4.Select the files or folders you would like to back up and copy them using the Copy command.
5.Create a folder on the external hard drive with the correct date in the name.
6.Paste all the copied files and folders into this folder.
7.Disconnect the external hard drive and store it in a safe location.
8.Repeat these steps on each scheduled backup day.
To recover the files from this backup, simply connect the backup hard drive to your computer and copy the damaged or missing data back onto your storage device.
The problem with using Copy and Paste to back up your data is that the backups must be done manually. As a result, it is possible to forget to create backups. These backups will also be much larger, since each backup will contain all the files and folders you copied, even if some of these folders have not changed since the previous backup.
These problems can be solved by using a backup utility such as Windows 10’s Backup and Restore.
 Guided Activity 10.2
Guided Activity 10.2
To use Backup and Restore:
1.Buy an external hard drive to use for the backup and connect it to your computer.
2.Open the Start menu and enter the words Control Panel. This will open the window.
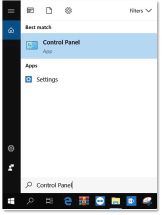
3.Click on the Backup and Restore (Windows 7) option to open the Backup and Restore window.
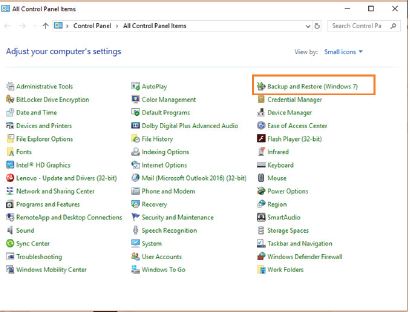
4.Click on the Set Up Backup option.
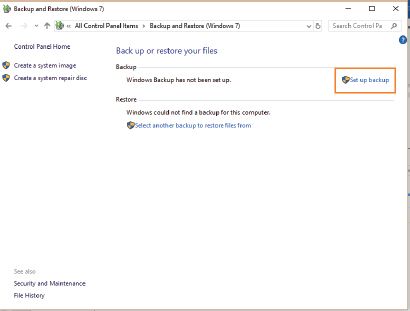
5.Select the external hard drive as the location where you would like to save the backup.
6.If all your files are stored in your private folders (such as the Documents, Music and Videos folders), use the Let Windows Choose option. Otherwise, select the Let Me Choose option and manually choose the folders that should be backed up.
7.Click on the Save Settings and Run Backup option to create a backup of all your files.
 Guided Activity 10.3
Guided Activity 10.3
To restore files from a Windows backup:
1.Connect your external hard drive to your computer.
2.Open the Backup and Restore (Windows 7) application from the Control Panel.
3.Click on the Restore All Users’ Files option.
4.Click on the Browse for Files or Browse for Folders option.
5.Tick the In the Original Location box and press Restore.
This will restore your files to where they used to be, thus replacing all lost files.
USING CLOUD STORAGE FOR BACKUP
One of the problems with backing up your computer’s contents to an external hard drive is that your computer and the drive can be lost due to theft, flood or fire. Cloud storage puts your information on an off-site server that never goes offline and that can be accessed from anywhere through the internet.
Cloud storage, however, is not the same as cloud backup. Although they both work on a similar basis and the result is the same – storing files online – there are completely different reasons for using them.
With cloud storage, you choose which files you want to store online and you send them to your online account. When you delete a file that you stored online, it is still in your cloud storage because it is not really tied to your computer anymore. Cloud backup is when you install a program on your computer and you tell it to keep certain files backed up online. A backup service will also upload any changes that are made to those files so that the current version is always online.
A backup server works for people or businesses that have a lot of files they want to keep backed up online, so that, should one of the computers suddenly stop working, the files can still be obtained from the cloud backup server.
These are a few cloud storage providers:
- Google Drive: This works very well with Google products and you get 15 GB for free, after which you have to pay a monthly fee for more storage space.
- Apple iCloud: This service works with all Apple devices, whether a Mac, iPhone, iPad or iPod. You get 5 GB for free but have to pay for more than that.
- Dropbox: It gives users 2 GB for free and lets you access your files from the Web, your desktop or mobile devices.
- Microsoft OneDrive: Integrates well with Microsoft’s products such as SharePoint and Word. Everyone with a Microsoft account gets 5 GB free storage space, after which you need to subscribe and pay for more space.
 Activity 10.2
Activity 10.2
Answer the following in your own words.
1.Is it really necessary to back up the content of your computer? Why or why not?
2.Talk to at least two people you know who have their own computers.
a.Find out if they back up their information? Why or why not?
b.What do they back up?
c.How many times do they back up their information?
d.How do they back up their information?
3.What would be a practical and workable solution for you to back up your information?
UNIT
10.3 Protecting yourself online
ONLINE HARASSMENT, STALKING AND BULLYING
Online harassment is a wide range of damaging behaviours such as hateful messages, distributed denial-of-service (DDoS) attacks, defamation and others. The goal of the harasser is to drive the target off the internet or punish them by publishing personal information, sending threats, or promoting harm.
Online harassment is especially prevalent in young adults; with people of colour and women more likely to be victims of serious harassment.

ONLINE HARASSMENT
HOW DO YOU AVOID ONLINE HARASSMENT?
Limit the personal data you share on social media accounts and review your security or privacy settings regularly. Do not post your physical address, mobile number or email address (or make them publicly available as part of your profile).
Choose your passwords wisely, make them unique and strong. Change passwords regularly and do not use the same password for different sites. Make sure that the answers to your secret questions are hard to guess.

Something to know
A study that was done in 28 countries, including South Africa, in 2018, found that South Africa showed the highest prevalence of cyberbullying, with an increase of 24% from 2011. This could be attributed to the increased use of social media in South Africa.
WHAT TO DO IF YOU ARE HARASSED?
Make a copy of everything. Take screenshots of the harassment and print them out. Keep a record of the websites where the harassment happened. Have your parents take a look at the posts. Report the bullying to the website and ask that they take the harassing content down. If necessary, take the evidence you have collected to the police to open a case.
If you are bullied or harassed, you can call Childline South Africa on 0800 055 555.
MALWARE (MALICIOUS WARE)
Malware is any software that is specifically designed to disrupt, damage or gain unauthorised access to a computer. Examples of malware are:
1.Viruses
2.Worms
3.Trojans
4.Scareware
5.Spyware
6.Adware
7.Ransomware
To prevent your computer from becoming infected with malware, computer experts suggest that you do the following:
- Do not open suspicious emails.
- Do not download suspicious programs or attachments.
- Keep your antivirus application up to date.
- Keep your other software up to date: Hackers can use software weaknesses or vulnerabilities to gain access to your computer.
MULTI-STEP VERIFICATION
Two-factor authentication, or multi-step verification, prevents anyone from logging into your accounts using just your username and password. Instead, they need a second factor (which is usually a physical device such as your phone) to access your account.

CYBERBULLYING
Teens Talk: What works to stop cyberbullying?

https://cyberbullying.org/teens-talk-works-stop-cyberbullying
What is cyberbullying?

https://www.pacerteensagainstbullying.org/experiencing-bullying/cyber-bullying/
 Activity 10.3
Activity 10.3
1.Read the following case study and answer the questions that follow.
Thando is a young woman who has always had weight and confidence issues. After she decided to improve herself and started following an exercise and diet regime, her friends encouraged her to take photos of herself to show the world her new-found body and self-confidence. Thando decided to share her progress and photos with her friends and family. When she uploaded her new photos on Facebook, a lot of people liked them. Unfortunately one person started to post horrible comments about her appearance and character.
When Thando’s sister saw these comments, she became worried that they would affect her sister’s new-found confidence and her mental and physical health. She decided to talk to Thando about possible solutions to the problem. Both Thando and her sister eventually reported the person to Facebook and asked that Facebook remove that user’s offensive comments and block their account.
a.Have you experienced some kind of cyberbullying or harassment, or do you know of someone who has experienced it? Tell the story.
b.Is it a problem in South Africa, or is it becoming a problem? Why do you say so?
c.What can you as a young person do to prevent this from becoming a problem?
d.What can you do if you learn that someone is being bullied?
e.What must you do if you become the target of cyberbullying and harassment?
2.Is there something that you can do to stop cyberbullying at school? Come up with a school project.
UNIT
10.4 E-commerce and e-banking
When using online services such as online banking or shopping, you must be careful that your information is not stolen. Your banking or credit card information can be used to make multiple purchases.
Tips for safely using online banking and shopping include:
- Use proper antivirus software and make sure it is up to date.
- Do not log into online banking or shopping sites using public Wi-Fi or on public computers (like those in an internet café).
- Make sure that the operating systems on all your devices are up to date. This is important for both your phone and computer. Make sure that the banking app on your phone is also up to date.
- Change your passwords regularly and make sure they are strong.
- Do not sign into your banking account through a link in an email as this is most likely a phishing attack.
- Sign up for notifications on your bank account for when money comes in or goes out and when your account is accessed online.
You should always check that the website URL has an “https” extension whenever you are making a transaction online. The “s” stands for secure and it means that the website has something called a Secure Sockets Layer (SSL) certificate. This creates an encrypted link between you and the server, making the data that you and the server send and receive secure and private. This protects your data from being intercepted and stolen.
ADVANTAGES OF E-COMMERCE
Below are some of the advantages that e-commerce holds for the consumer, which is you.
- There is a very wide range of products and services available.
- There are no geographical limitations. It is just as easy to buy something from the USA or Europe as it is to buy it in South Africa.
- It definitely saves you time, for example travel time, waiting time and searching time.
- It is available 24/7.
RISKS OF E-COMMERCE
Unfortunately, there are also certain risks related to e-commerce, such as:
- Fraud: Because transactional data is transmitted over the internet, it has become one of the target areas of cybercriminals. Financial information can be hacked or stolen, leading to purchases made by people who are not the rightful owners of that information. Customers sometimes complain that they have not received their packages and it is difficult to determine whether that is true or not.
- Online security: There are many security threats such as malware, spam mail and phishing that can cause you harm.
- Exchanging a product that does not fit the online description can be difficult.

INTERNET BANKING
ADVANTAGES OF E-BANKING
Below are some of the advantages of internet banking:
- It is convenient, as customers have 24-hour access to the bank, seven days a week.
- It can be done from any location where you have Internet.
RISKS OF E-BANKING
Although online banking is secure enough to use on a daily basis, you should know about these risks:
- Fraudulent transactions
- Online theft of your access ID/user ID or PIN/password could happen.
- Banking apps can be compromised.
 Activity 10.4
Activity 10.4
Answer the following in your own words.
1.What exactly does e-commerce mean?
2.What are the advantages of e-commerce?
3.What are the risks of e-commerce?
4.What can you do to make sure that you are safe when shopping online?
UNIT
10.5 How antivirus programs work
Antivirus software is any computer program that is designed to scan for, isolate and delete any harmful program from your computer before it causes any damage, but you can do an active scan any time you think that your computing device has been infected with a virus.
Antivirus and antimalware programs check all the files on a computer, checking all changes and the memory for specific types of file change patterns.
APPLICATION PERMISSIONS
When you install an app on your smartphone or tablet, you will need to give it permission to access certain functions on your device. For example, when you install a navigation app (such as Google Maps), you will first be asked for permission to access the device’s GPS location.
Using app permissions means that you can control what capabilities or information the app can access.
 Activity 10.5
Activity 10.5
1.Give two examples of ways to avoid online harassment.
2.What is malware?
3.How do you avoid getting a malware infection?
4.What is multi-step verification?
5.Give five tips for safe online banking.
6.What does the “s” in “https” mean?
7.Briefly describe three common types of virus detection in antivirus programs.
REVISION ACTIVITY
QUESTION 1: MULTIPLE CHOICE
1.1Which of the following is NOT an example of social engineering? (1)
A.Phishing
B.Malware
C.Tailgating
D.Pretexting
1.2If you come across fake news, what should you do? (1)
A.Post it and share it
B.Do more research on it
C.Delete it from the internet
D.Edit and try to fix it
1.3Which of the following institutions is used in phishing scams the most? (1)
A.Banks
B.Universities
C.Kindergartens
D.Online shops
1.4Which of the following scenarios do NOT use online banking? (1)
A.Ahmed owns an electronics store and does have a card swipe machine.
B.Chloe does not have a physical clothing store but she sells clothing through an online website.
C.Blessing only likes shopping for games online.
D.Hanno wants to send money to his mother overseas.
1.5Which of the following is NOT an antivirus program/application? (1)
A.Avast
B.Norton
C.Bitdefender
D.OneDrive
QUESTION 2: TRUE OR FALSE
Write True or False next to the question number. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word NOT to change the statement.)
a.Multi-step verification can be used to keep your email password secure. (1)
b.A disadvantage of e-commerce is that it is hard to send physical money online. (1)
c.Emails from an unknown source are known as suspicious emails. (1)
d.If you want to prevent people from accessing your online accounts, you must use a strong password. (1)
e.Hackers use Quid Pro Quo to steal passwords. (1)
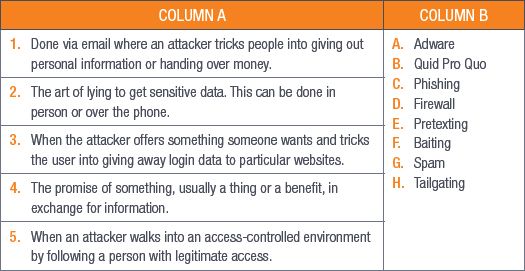
QUESTION 3: MATCHING ITEMS
Choose a term/concept from Column B that matches a description in Column A. Write only the letter next to the question number (e.g. 1J). (5)
QUESTION 4: MEDIUM QUESTIONS
4.1Briefly explain how to recover data from a backup? (2)
4.2What are three disadvantages of using an external hard drive to back up your computer’s data? (3)
4.3What is a preferable alternative to physical computer backups? (1)
a.Explain what this alternative backup does. (3)
b.Who would benefit most from this type of alternative backup? Mention three of them. (3)
c.What three things can you do to prevent your computer from getting infected by malware? (3)
4.4What is the difference between e-commerce and e-banking? (4)
4.5List two risks of online banking. (2)
4.6Explain the concept of cloud storage. (2)
4.7Provide two examples of cloud storage providers. (2)
TOTAL: [40]
AT THE END OF THE CHAPTER

|
Previous
Chapter 9: Errors and bugs
|
Table of Contents |
Next
Chapter 11: Internet and the World Wide Web
|





